
Stop Equipping Our Enemies - Protecting CUI is Critical
Federal agencies routinely generate, use, store and share information that, while not meeting the threshold for classification as national security or atomic energy information, requires some level of protection from unauthorized access and release. The Department of Defense (DoD) has determined the compromise of this contract-related information is enabling and equipping our enemies.
Important Recent Updates
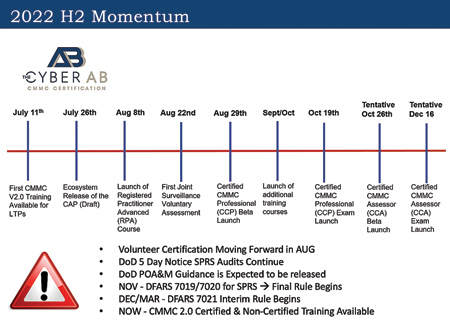
On July 26, 2022, the CMMC-AB now renamed the Cyber AB and announced very important updates combined with recent enforcement activities continuing by the DoD and OEMs. The DoD is expected to announce its limitation or restriction of certain uncompleted requirements on the plan of action and milestones. It is not known if the DoD will allow a set period of time for contractors to complete those tasks, or if they will immediately become non-compliant with DFARS flow-down requirements. Contractors are being determined to be ineligible to bid and current work is being redirected to compliant subcontractors. "Time is short, the standards are complex and tier suppliers over the next 6-12 months will be either growing revenue that was redirected from ineligible competitors or losing it," said Mark Boothe, President of TeamLogic IT of Dallas.
What is CUI?
Controlled Unclassified Information (CUI) is information received and developed in performance of defense contracts or subcontracts with military or aerospace applications that are restricted within the contract terms. Two common categories of CUI include Controlled Technical Information and Export Controlled information, which include technical drawings, part numbers and much more. According to the Defense Counterintelligence Security Agency CUI FAQ, anyone who creates information that is considered CUI is responsible for protecting and handling it and all active contracts should have CUI requirements in place. A lack of training and understanding of the CUI requirements is increasing most companies' risk exposure by creating and disseminating unmarked CUI.
Who is responsible for CUI?
Only Authorized Holders, as organizations or individuals, with lawful government purpose can view, create, store, share or otherwise disseminate CUI in conjunction with the contract performance. To become an Authorized Holder, employees must be screened and meet specific requirements. They must be trained and knowledgeable on how to handle and protect CUI prior to granting access.
Stop Equipping Our Enemies - Protecting CUI is Critical
The U.S. government and the DoD began implementing the CUI program in 2010 after seeing how much covered defense information had been stolen by our adversaries. To prevent unauthorized disclosure, every company in the Defense Industry Base (DIB) must protect CUI and document their compliance according to the requirements.
Where Do We Start, or Start Again?
The process and evidence expected by the DoD to demonstrate compliance and conformity is complex, technical and detailed. The first and most important step involves identifying the CUI your company receives and develops in performance of the contract, then conduct the required annual risk and security assessments that assess both technical safeguards and business practices. Then the Plan of Action and Milestones (POAM) sets a path to close non-conforming issues. Finally, those documents are integrated into the System Security Plan (SSP)-a living document that details and governs all the required activities for compliance and conformity.
After Four Years, DoD Enforcement Begins with 5-Day Notice Audits
In 2017, DoD introduced the Defense Federal Acquisition Regulation Supplement (DFARS) contract clause 252.204-7012. This required contractors and all impacted subcontractors to "self-attest" that they were complying with the CUI security requirements. The deadline to self- attest was December 31, 2017, and those attestations may be creating more risk exposure for companies.
In November of 2020, a new requirement intended to enforce the compliance stated, "In order to be considered for award, the Offeror shall have a current assessment and post summary level score for a DoD Assessment in the Supplier Performance Risk System (SPRS) on each covered contractor information system that is relevant to the offer, contract, task order, or delivery order." This requirement is being aggressively enforced by prime contractors.
The DoD is expected to begin 5-Day notice audits of evidence to support SPRS scores and missing scores in a few months. The DoD states that 75% of DIB companies are reporting a "perfect score," but previous audits have found that 75% of the companies reviewed have "serious deficiencies" within their programs. Now, the DoD seeks to assess and validate the evidence supporting a company's score. Any penalties resulting from these audits that will begin in the next few months, and any corrective actions issued will be monitored by the prime contractor and the DoD program's contracting officer.
Enforcement is a Growing Concern for Most DIB Companies.
While most DIB companies have legally attested, they were compliant, industry experts estimate that 90% or more are not because they do not fully understand the requirements and the evidentiary standard expected by the DoD. Tier suppliers and companies are "waking up" to recognize the risk exposure and significant investment of time (12-18 months) and resources needed to fully meet requirements, but genuine expertise and reliable guidance is scarce and quickly growing in demand.
DoD will Require CMMC Certification
In 2020, the Defense Department introduced the Cyber Maturity Model Certification (CMMC) program to assess and certify compliance and conformity with the CUI security requirements. A group of industry volunteers worked to establish the CMMC Accreditation Body, recently renamed the "Cyber AB" which is responsible for management and oversight of the CMMC certification ecosystem. Regan Edens served as a Director on the Board of Directors and also led the development of the standards and training programs to help improve clarity about the CUI security requirements and consistency in certification standards.
"As Edens and others trained most of the provisional third-party assessors, there is still a great deal of effort ahead for government and industry to work together to meet the requirements to improve our nation's security posture surrounding DoD contracts," said Boothe. When fully rolled out, without certification, no company will be eligible to receive or maintain a DoD contract involving CUI.
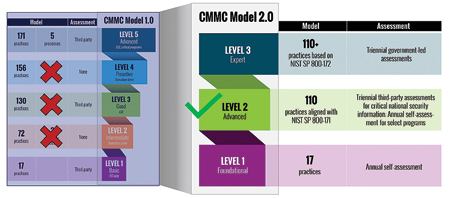
In 2021, CMMC 2.0 changes limited the focus for certification to the federal standard by removing the 20 extra controls. "This landscape is still evolving, so companies should carefully consider outside assistance to reach compliance," said Boothe. "Manufacturing companies will need to find outside consultants and IT Managed Service Providers if they do not have sufficient internal resources to meet these new requirements."
Changes in DoD Oversight and Federal Enforcement
Oversight of CMMC moved under the DoD CIO, which provides much tougher enforcement capability against companies that claim to be compliant but are not. The Federal False Claims Act and recently established Department of Justice Cybersecurity Fraud Task Force also provides an avenue for civil and criminal penalties for DIB suppliers and contractors.
CMMC Warnings and Indicators for the DIB - Far Harder than Expected
The certification of CMMC Third-Party Assessor Organizations (C3PAO's) has proven to be far more difficult than expected. The DoD assessors stated during an industry conference, that there is a fundamental gap between the DoD and those organizations being assessed on the scope and detail of evidence required to demonstrate compliance and conformity. The DoD is establishing a high standard and currently just over 250 assessor candidate companies have certified. A recent surge in passing audits demonstrates the C3PAO's have adjusted to the steep learning curve and are far more prepared. The DoD has improved on its communication of its expectations and industry experts believe a far more aggressive wave of activity will begin with the 5-Day Notice Audits of SPRS scores announced by DoD in March 2022. Quietly, the DoD fully expects supply chain consolidation as companies are weeded out who cannot meet CUI security requirements.
POA&M Restrictions and Limitations are Coming Soon
Also in March 2022, the Defense Contract Management Agency (DCMA) announced changes to allowable items on the POA&M and limitations to the time period for full compliance are also coming soon. Some items will be restricted from being on a POA&M and some items will be allowed to be completed within an expected 180 days.
Reports of large prime contractors refusing to award new contracts, limiting contracts and ending contracts are growing louder and louder among DIB companies. While companies are allowed to have items on their POAMs, they should be moving now to fix the largest and most difficult roadblocks to compliance. DoD has been moving toward enforcement at a quicker pace as the DIB remains largely non compliant more than four years since the DFARS deadline in 2017.
There is Good News - Competitive Advantages are Emerging Now
As a result of "everyone claiming" compliance with CUI security requirements, prime contractors are beginning to recognize the significant risk created across their supply chains. Even after four years, the good news for companies that can demonstrate proof of compliance through competence and evidence are often seeing 40-60% gains in their top line revenue growth, according to Edens who also leads DTC Global, a specialty advisory firm for companies to meet these requirements. "By demonstrating competence and gaining the confidence of customers, contracting officers, buyers and higher-tier suppliers are choosing the worry-free choice for contract awards," said Edens.
Companies that meet CMMC requirements are in a strong position to ask the prime, higher sub- and contracting officer to check competitors to see if they can prove their compliance. The way Boothe sees it: "If competitors are not yet meeting the required CMMC level but your company is compliant, you are now better position to win business that would have otherwise gone to someone else. Since the CMMC requirements flow down throughout the supply chain, DoD primes and high-level subs do not want to spend time chasing down non compliant subs. Once they find one, they can move on to doing what they do best."
"Like Sarbanes Oxley and financial audit controls, CMMC will become that standard for data security. And we all know the most valuable commodity a company has in 2022 is data. Protect it and win," continued Boothe.
Article authored by TeamLogic IT
and DTC Global
For more information contact:
Mark Boothe, President
TeamLogic IT Dallas, TX
12700 Hillcrest Road
Suite 125
Dallas, TX 75230
972-793-8529
mboothe@teamlogicit.com
www.TeamLogicIT.com/DallasNorthTX
Regan Edens
Chief of Transformation & Compliance
DTC Global
214-390-6881
reganedens@dtcglobal.us
dtcglobal.us/