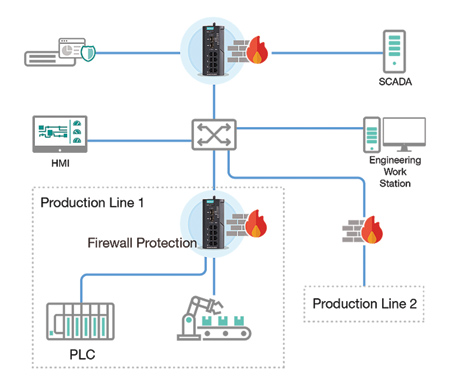
Building security boundaries to protect production lines without impacting each other when cybersecurity incidents occur
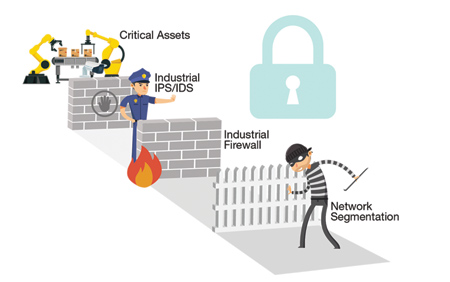
The defense-in-depth security concept is based on multiple layers of security mechanisms that increase the security of the entire system
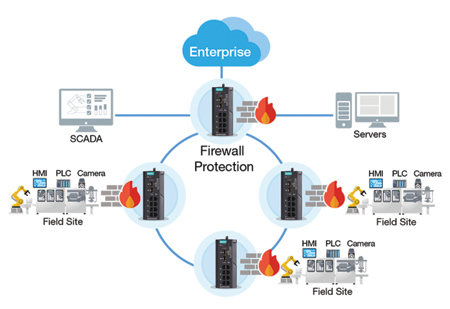
The rise of interconnected Operational Technology (OT) and Information Technology (IT) systems is often attributed to how business models have evolved to enhance operational efficiency. For example, SCADA networks deployed along oil pipelines now collect oil output data that is essential to billing and pricing systems. This increase in data collection allows companies to predict with higher levels of accuracy not only oil production and output, but also expected revenue.
However, these interconnected systems do not only bring benefits. A downside is that the likelihood of introducing cybersecurity threats to OT systems increases significantly. Compromising IT systems can have a hugely negative impact on OT systems. Ransomware attacks, for instance, are increasing in their severity. This type of malware exploits Windows vulnerabilities and attacks insufficiently protected systems.
With more similar cybersecurity incidents occurring in OT systems, business owners and regulators are keen to seek solutions that enhance industrial cybersecurity and allow operations to keep functioning normally. Addressed here is the concept of "Defense-in-Depth" that allows businesses to leverage their existing network infrastructure to build the first line of network defense.
What is the Security Boundary Concept?
When enhancing cybersecurity, it is important to understand how industrial systems are exchanging data within different systems and how they connect to IT-level systems. In the most ideal scenario, when traffic crosses different systems, there should be boundaries in place between each system to ensure the traffic has good cyber hygiene, even if it is authenticated and authorized. However, it is challenging and often unrealistic to build boundaries between every system, as it involves significant expenditure and often has a detrimental effect to the efficiency of network communications. It is for these reasons that Moxa recommends the division of OT systems into different digital cells and zones, to build up the boundaries to find the right balance between expenditure and acceptable levels of risk.
The defense-in-depth approach, which is recommended by the IEC 62443 cybersecurity standard committee, is widely used across industries and has a good track record of helping build up multiple layers of protection to fulfill operational requirements. In one example, the critical assets and operations are considered the most important. Because they perform vital roles for businesses, it is wise to take additional security precautions, such as adding more layers of protection, to secure them further.
How to Build Security Boundaries: Network Segmentation/Physical Layer Segmentation
This is known as air gapping, when two networks are physically isolated. When the operations and security of one system needs to be independently maintained, an air gap is a potential solution. However, as mentioned earlier, it is increasingly difficult to arrange networks this way due to business and operational requirements.
Data Link/Network (Layer 2/Layer 3) Segmentation
Since industrial control systems may have been built decades ago, one of the key challenges, but also essential requirements for network administrators, is to leverage existing infrastructure while ensuring industrial control systems remain secure. One approach that is frequently deployed is to segregate traffic between different network segments using a VLAN (Virtual LAN), which is one of the functions of managed Ethernet switches. Some Ethernet switches feature Access Control Lists (ACL) at the port level, which can help improve VLAN security as data enters the switch. An alternative is to deploy firewalls to protect industrial applications and data especially when you need to deal with traffic on Layer 2 and Layer 3 networks.
Layer 4-7 Network Segmentation
Further segmentation can be applied through Deep Packet Inspection (DPI). DPI offers granular control over network traffic and helps you filter industrial protocols based on the requirements of the application. When you have multiple devices on the same network, theoretically, they all have the ability to communicate with each other. However, there are certain scenarios, when for example, Controller A should only communicate with Robotic Arm A at a specific time, then DPI technology can help engineers to define which controllers can perform read/write commands or even the direction of traffic.
Micro-Segmentation
In some situations, additional protection for critical assets is necessary, and a good way to achieve this is to use an intrusion prevention system to micro segment the network. What makes micro-segmentation particularly helpful for industrial networks is that it can be used to segregate the network into even smaller sub-networks. What is beneficial about this approach is that the virtual patch function of an IPS can help mitigate the risk of known vulnerabilities. For example, some systems might be operating on Windows XP, which Microsoft does not provide security updates for anymore. Under this scenario, even though there are known vulnerabilities, it may not be feasible to perform security updates.
Secure Remote Access
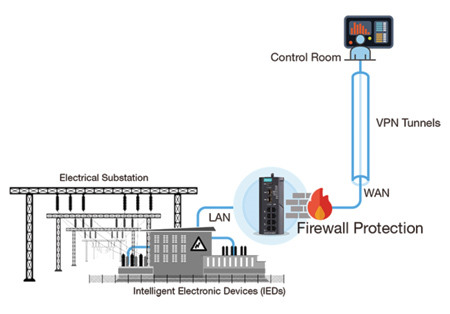
According to cybersecurity experts, remote desktop protocols are sometimes exploited to spread malware or conduct unauthorized activity. As remote connections have become more and more prevalent due to the necessity of increasing operational efficiency and the need to perform troubleshooting quickly, it is unsurprising that building security boundaries between two field sites is being talked about more frequently. Instead of using software to build the remote connections, which can easily lead to vulnerabilities in the long term, it is highly recommended to build VPN tunnels and ensure that access control mechanisms are maintained properly.
Typical scenarios:
- Manufacturing: Interconnected factory networks need proper network segmentation to reinforce industrial network security. Furthermore, network redundancy is also required to ensure the availability of the industrial control system.
- Secure Substation Monitoring: A power grid that covers a vast area needs IEC 61850 certified VPN solutions to monitor the intelligent electronic devices (IEDs) at each remote substation.
Since business owners are no longer able to enjoy the benefits and security of completely air-gapped networks, it is imperative for business owners and engineers to enhance security boundaries through different approaches including network segmentation, micro-segmentation, and secure remote access. Each of these approaches fulfills different network requirements and helps enhance cybersecurity, not just forming the perimeter protection but also preventing lateral movement of unauthorized traffic.
Authored by Moxa
For more information contact:
Moxa Americas
601 Valencia Ave, Suite 100
Brea, CA 92823
www.moxa.com